The Importance of Early Detection During Software Development

Detecting vulnerabilities has become an inherent part of the modeling, development, or implementation process of software. In terms of security, it’s important to remember that software is the outermost layer within a set of other dependencies, frameworks, programming languages, and operating systems that are also exposed and therefore can compromise the stability of the whole.
Ensuring that WOCU-Monitoring is protected against the changing landscape of code security attacks and failures has been, is, and will be one of the main concerns addressed since the initial versions.
Overview of Our Vulnerability Management Process
When addressing best practices during the development and deployment of WOCU-Monitoring, we come face to face with Continuous Integration (CI) environments. Our development process is geared towards incrementally adding functionality to the product. To ensure the software functions correctly and to verify the code quality within our agile workflow, a series of checks and adapted tests are run in a CI environment.
Recently, new measures have been integrated to strengthen and prevent attacks that may affect system security, by integrating into our CI the checking of installed dependencies for known security vulnerabilities. See the following example:
+==============================================================================+
| REPORT |
+============================+===========+==========================+==========+
| package | installed | affected | ID |
+============================+===========+==========================+==========+
| django | 1.2 | <1.2.2 | 25701 |
+==============================================================================+
| Cross-site scripting (XSS) vulnerability in Django 1.2.x before 1.2.2 allows |
| remote attackers to inject arbitrary web script or HTML via a csrfmiddlewar |
| etoken (aka csrf_token) cookie. |
+==============================================================================+This new subprocess will query the database where package vulnerabilities that are in use are registered, to detect or discard the existence of security risks. Additionally, necessary updates will be suggested to resolve any detected vulnerabilities. For us, it’s essential to know which dependencies and libraries we use and ensure they are updated with the latest security bug fixes.
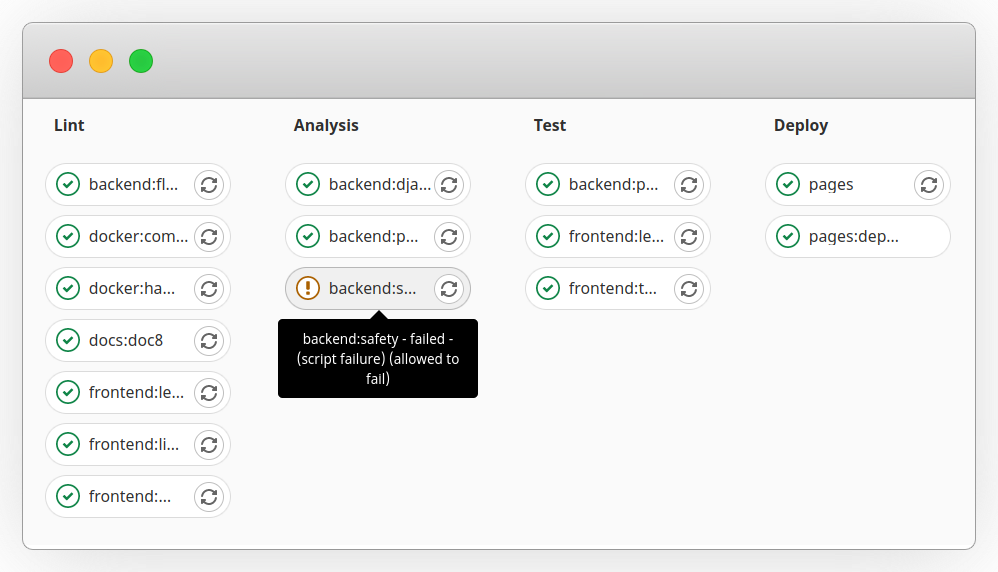
In essence, the CI will detect during the development phase any vulnerable dependencies, both in the backend and frontend, that may affect the security of WOCU-Monitoring and suggest relevant changes to address them, preventing them from going unnoticed for an extended period.
Prevent or Act?
Without a doubt, at WOCU-Monitoring, we opt for prevention during the development process of our projects, through the automation of proactive processes for early detection of vulnerabilities as quickly as possible.